21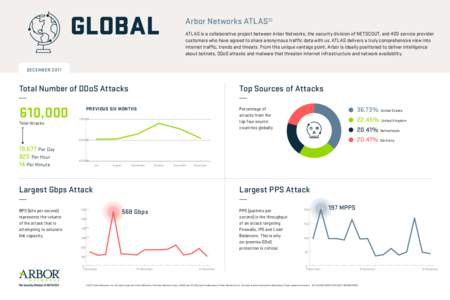 | Add to Reading ListSource URL: resources.arbornetworks.comLanguage: English - Date: 2018-01-04 13:54:43
|
|---|
22 | Add to Reading ListSource URL: 2sep653x2vim4375oc23b3j9-wpengine.netdna-ssl.comLanguage: English - Date: 2016-11-01 22:02:07
|
|---|
23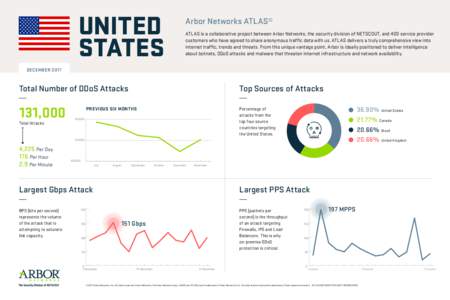 | Add to Reading ListSource URL: resources.arbornetworks.comLanguage: English - Date: 2018-01-04 13:55:03
|
|---|
24 | Add to Reading ListSource URL: www.adax.comLanguage: English - Date: 2016-12-14 05:34:20
|
|---|
25 | Add to Reading ListSource URL: www.escudocloud.euLanguage: English - Date: 2018-03-05 12:31:14
|
|---|
26 | Add to Reading ListSource URL: navysna.orgLanguage: English - Date: 2017-06-13 14:03:48
|
|---|
27 | Add to Reading ListSource URL: www.varmour.comLanguage: English - Date: 2016-10-12 16:54:47
|
|---|
28 | Add to Reading ListSource URL: www.escudocloud.euLanguage: English - Date: 2018-03-05 12:31:13
|
|---|
29 | Add to Reading ListSource URL: www.dss.milLanguage: English - Date: 2017-07-19 13:54:52
|
|---|
30 | Add to Reading ListSource URL: www.iwsinc.comLanguage: English - Date: 2016-11-14 11:05:48
|
|---|